Practical HTTP Host header attacks
Wed, 04 Jun 2014 20:42:31 +0200 last edited: Wed, 04 Jun 2014 20:42:32 +0200
You can trust really nothing. 
#^Skeleton Scribe: Practical HTTP Host header attacks

#^Skeleton Scribe: Practical HTTP Host header attacks

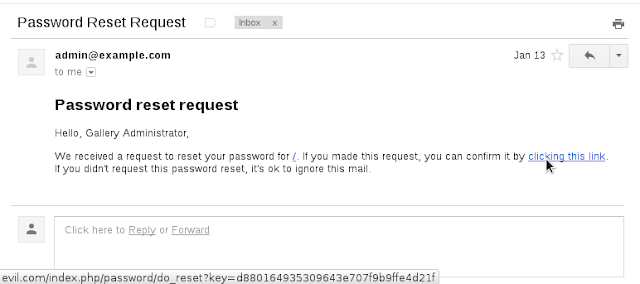
How does a deployable web-application know where it is? Creating a trustworthy absolute URI is trickier than it sounds. Developers often resort to the exceedingly untrustworthy HTTP Host header (_SERVER["HTTP_HOST"] in PHP). Even otherwise-secure applications trust this value enough to write it to the page without HTML-encoding it with code equi...
This website is tracked using the Piwik analytics tool. If you do not want that your visits are logged this way you can set a cookie to prevent Piwik from tracking further visits of the site (opt-out).

I've got basically two and a half years of experience. At that point, most people are still churning out six SQL injection attack vectors an hour. Conversely, I spend most of my time figuring out how to mitigate against an idiot drooling on their keyboard.
That's not to say there aren't bugs in my code. There are - just they're actual bugs, not trust. Bugs are for Christmas, trust is for life.